
As per the latest alert from the American Cybersecurity and Infrastructure Security Agency (CISA), Russia’s Snake has infected a network of computers. Read to know more about the devious malware.
What is Snake?
Snake is a cyber espionage tool developed by the Russian Federal Security Service. As per American Cybersecurity and Infrastructure Security Agency (CISA), the implant is the “most sophisticated cyber espionage tool designed and used by Center 16 of Russia’s Federal Security Service for long-term intelligence collection on sensitive targets”. It was developed in 2003 for conducting cyber espionage against NATO, government agencies, private companies, media organizations, research institutes, and financial services among others. It moves as an elegantly designed code and has complex technicalities allowing it to go undetected.
So far snake has been detected on Linus, macOS, and Windows computers in over 50 nations. This malware is a simple concept cloaked in a masterful technical device. Espionahe teams put the malware on the target device to copy information of interest and send it to Russia. Since its creation, cyber spies have regularly updated it ensuring evasion. The current version is extremely cunning and persistent in evading detection. Additionally, the risk of ‘snake’ moves beyond intelligence collection with its ability to disrupt critical control systems managing water, energy, hospitals, and buildings.
More on the devious malware
On May 9, the Department of Justice announced the Federal Bureau of Investigation’s success in disrupting the global peer-to-peer snake infection. The covert network was allowing infected systems to collect sensitive information and send it to spy matters. While the use of custom communication protocols allows the snake malware to stay covert, the FBI has been under increasing scrutiny since the war in Ukraine. The FBI also received a court order for dismantling Snake as a part of MEDUSA. PERSEUS, a tool developed for countering the malware ensures Snake disables itself, stopping the infection network.
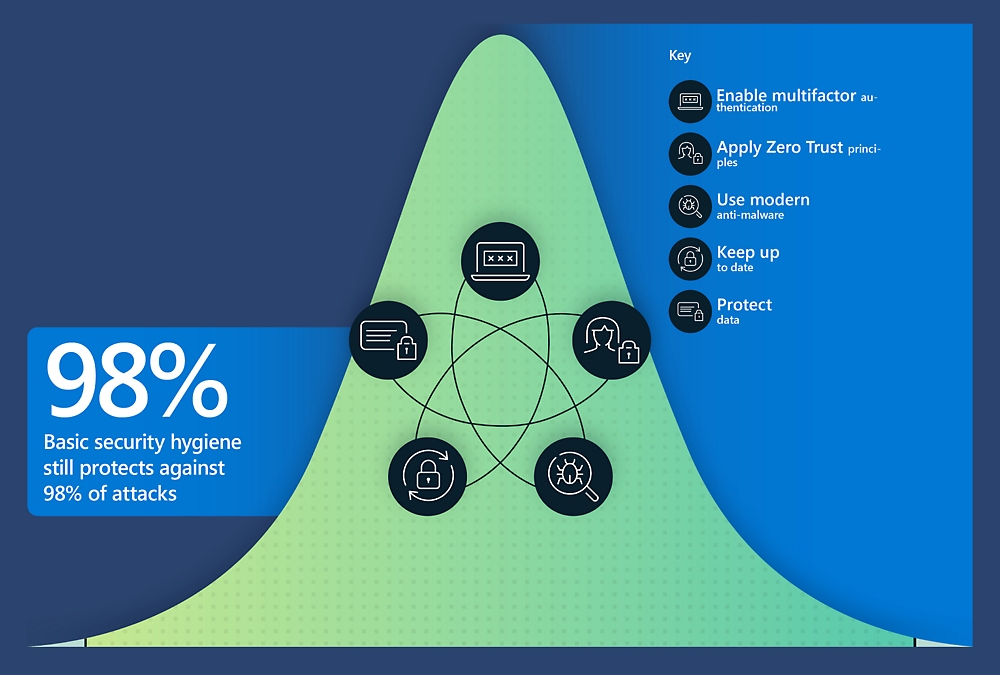
Luckily, effective cybersecurity inserts are not very complicated. According to Microsoft, there are five easy steps to ensuring your devices have about 98 percent of cybersecurity attacks. Enabling multi-factor authentication on all applications and online accounts is very important. This also increases the login process, providing more levels of security. Practicing “zero trust” and authenticating, validating, and authorizing all system users is vital. The tech giant also recommends the use of modern anti-malware applications and keeping your systems up to date. Finally, protecting your data by making copies of vital data is important.


